Home
Lehre
MNM Team
Projekte
ATV2 Cluster
DASH
Embedded MSec Lab
PROCESS
QuaSiModO
Previous Projects
Publikationen
en
The Embedded Multicast Security Lab
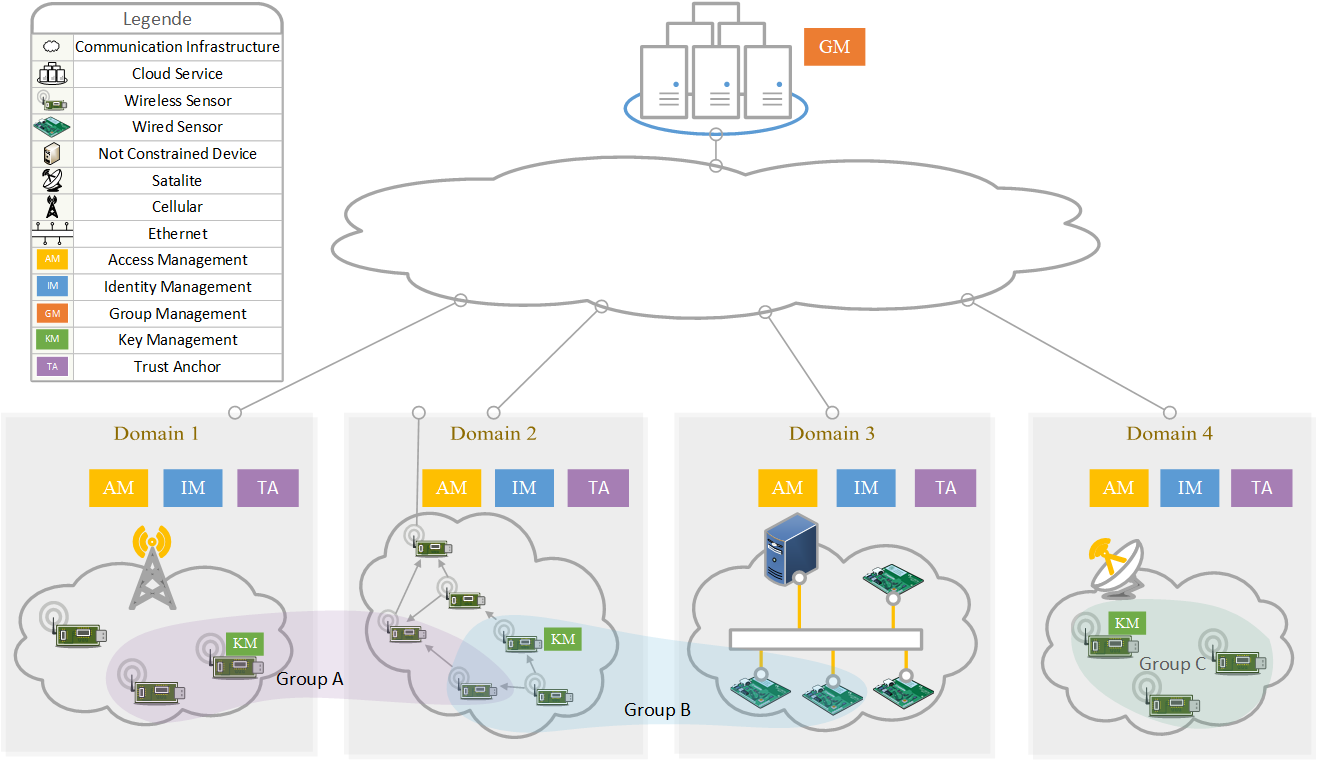
Securing group communication in constrained networks requires new solutions to be found, implemented and evaluated. This is especially true when group communication is desired, which turns out to be much more difficult to secure than point-to-point communications, as the sharing of keys along the group potentially lowers the security of the solutions. There is a variety of work on security in constrained networks, but most of them only pick one particular security property (e.g. μTesla) or are simply designed for a very specific use case (e.g. Group-DTLS for the lightening industry). This is especially true for group communication, which is a niche, but turns out to be very attractive for constrained networks.
Smart Homes, Cars, Factories, etc. are networks of such devices acting as one system from an outside point of view. Applying well known models of informatics, this networks can be seen as administrative domains (ADs). Following this idea, the owner of a certain system (e.g. the owner of a Smart Home) acts as the administrator to the system, who in turn should decide on who to give access the system and its data. In current deployments, this access is usually managed on top of the cloud instance by registering an external actor (e.g. a smartphone) with access to the cloud service. The external actor sends control messages or data requests to the cloud, acting as some sort of "proxy" forwarding or translating the messages to the constrained device or the network.
Testbed
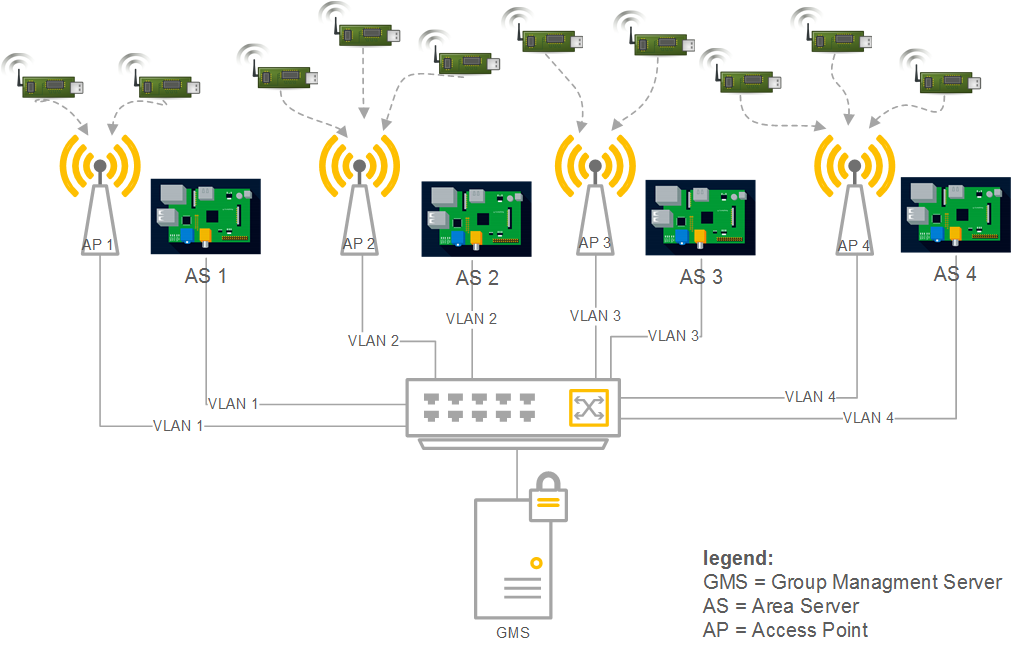
With multicasting being an interesting option for many use cases, we are currently developing a testbed, allowing flexible deployment of group communication scenarios and implementations of different solution for secure group communication. The testbed contains devices with different constraints, such as different microprocessor architectures - namely ARM Cortex M0 and ATmega328P, but also single board computers with the ARMv7 and ARMv8 architectures. They all communicate wired (Ethernet) or wireless (Bluetooth or WiFi). The testbed is able to simulate different kinds of communication groups:
- spatial
- a group of devices connected to one and the same access point. Each AP is managed by an Area Server (AS) separated with VLAN.
- logical
- a group of devices sharing information using IP multicasting and being managed by the Group Management Server (GMS).
- secure
- a group of devices sharing secure information using IPsec, being managed by the GMS, implemented on constrained devices.
Hardware
Computing Hardware:
| Device | Architecture | Clock Speed |
Flash Memory |
SRAM |
|---|---|---|---|---|
| Arduino Uno |
ATmega328 | 16MHz | 32KB | 2KB |
| Arduino M0+ |
ARM Cortex-M0+ | 48MHz | 256KB | 32KB |
| Arduino Due |
ARM Cortex-M3 | 84MHz | 512KB | 96KB |
| ST NUCLEO-F091RC |
ARM Cortex-M0 | 48MHz | 256KB | 32KB |
| ST NUCLEO-F103RB |
ARM Cortex M3 | 72MHz | 128KB | 20KB |
| ST Nucleo F401 |
ARM Cortex-M4 | 84MHz | 512Kb | 96Kb |
| ST Nucleo144-F429 |
ARM Cortex-M4 | 180MHz | 2Mb | 256Kb |
Network Modules
- Semtech SX1272 868/915MHZ Lora MBED SHIELD
- Texas Instruments SimpleLinkWi-Fi CC3200
- Microchip AT86RF233 Zigbee / 802.15.4
- WIZnet Ethernet-Module W5100
- SparkFun nRF51822 Bluetooth / 802.15.1
Controller Hardware:
| Device | Architecture | Clock Speed |
Flash Memory |
SRAM |
|---|---|---|---|---|
| Raspbery Pi v1 |
ARM1176JZF-S | 700MHz |
256MB | |
| Raspbery Pi v3 |
ARM cortex-a53 | 1.2GHz Quad Core |
1GB | |
| Beaglebone Black |
Cortex-A8 + Dual PRU | 1000MHz | 4GB |
512MB |
Networking Hardware
- Netgear Prosafe GS748T Switch
- Colubris MAP-625 Access Point
- Laird Sentrius RG1 LoRa-Enabled Gateway
- Digi CONNECTPORT X4 Gateway - ZigBee to Ethernet
Current activities
- Design, Implementation and Evaluation of a Identity Based Signature (IBS) Scheme for group communication in constrained environments
- Implementation and Evaluation of G-IKEv2 for Strongswan
- Implementation and Evaluation of Walnut DSA for RIOT, FreeRTOS and Linux
- Implementation and Evaluation of Diet-ESP for RIOT and Linux
Publications
- Guggemos, T., Streit, K., Knüpfer, M., gentschen Felde, N., Hillmann, P., No Cookies, just CAKE: CRT based Key Hierarchy for Efficient Key Management in Dynamic Groups , In 13th International Conference for Internet Technology and Secured Transactions (ICITST-2018) , 2018, 13, 24-32, 12, 2018.
- gentschen Felde, N., Grundner-Culemann, S., Guggemos, T., Using identity-based signatures for authenticated group communication , In 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob 2018), Limassol, Cyprus, 10, 2018.
- Guggemos, T., Dynamic Key Distribution for Secure Group Communications in Constrained Environments, In Doctoral Consortium: Doctoral Consortium on e-Business and Telecommunications, 2018, SECRYPT, ICETE, Porto, Portugal, 07, 2018.
- gentschen Felde, N., Guggemos, T., Heider, T., Kranzlmüller, D., Secure Group Key Distribution in Constrained Environments with IKEv2, Proceedings of 2017th IEEE Conference on Dependable and Secure Computing, IEEE, Taipei , Taiwan , 08, 2017.
- gentschen Felde, N., Guggemos, T., Kranzlmüller, D., Secure Group Communication in Constrained Networks - A Gap Analysis , In Proceedings of the 1st IEEE GLOBAL IoT SUMMIT, 2017, IEEE Xplore, IEEE, Geneva, Switzerland, 06, 2017.
- Guggemos, T., Migault, D., Killian, S., Laurent, M., Diet-ESP: IP Layer Security for IoT , Journal of Computer Security, 2017(25:2), IOS Press, Amsterdam, Netherlands, 05, 2017.
- Migault, D., Palomares, D., Guggemos, T., Efficient Security for Homenet IoT and M2M Communications , In Proceedings of the 11th ACM Symposium on QoS and Security for Wireless and Mobile Networks, 2015(15), Q2SWinet 15, 9-17, ACM New York, ACM, Cancun Mexico, 11, 2015.
Student Work
Master Thesis
- Reding, J.-L., Verwaltung digitaler Schlüssel im Internet der Dinge mit einer Blockchain, Ludwig-Maximilians-Universität München, 09, 2018.
- Grundner-Culemann, S., Identity-based source authentication in constrained networks, Ludwig-Maximilians-Universität München, 10, 2017.
Bachelor Thesis
- Enzinger, M., Efficient group rekeying with G-IKEv2 and LKH, Ludwig-Maximilians-Universität München, 11, 2019.
- Munisamy, E., Parallel Execution of RSA Encryption on the GPU of the RPi, Ludwig-Maximilians-Universität München, 11, 2019.
- Rixen, Y., SIMD processing of AES on the Raspberry Pi, Ludwig-Maximilians-Universität München, 11, 2019.
- Meixner, W., Portierung und Entwicklung eines CC3200 Treibers für RIOT-OS, Ludwig-Maximilians-Universität München, 10, 2019.
- Malkus, M.-M., Implementing IPsec ESP in RIOT OS, Ludwig-Maximilians-Universität München, 09, 2019.
- Polack, C., An IoT Test Bed with Heterogeneous Embedded Platforms and Network Technologies, Ludwig-Maximilians-Universität München, 09, 2019.
- Dellinger, J., Streaming Multicast Authentication with TESLA and ESP on Linux, Ludwig-Maximilians-Universität München, 11, 2018.
- Schütze, C., Evaluation von Multicast Authentifizierung in Smart Homes mit dem TESLA Protokoll, Ludwig-Maximilians-Universität München, 11, 2018.
- Melnikov, A., A Testbed for Evaluating ID-based Authentication in Constrained Networks, Ludwig-Maximilians-Universität München, 07, 2018.
- Treutner, T., Evaluation effizienter Schlüsselbäume für hierarchische identitätsbasierte Signaturen im IoT, Ludwig-Maximilians-Universität München, 06, 2018.
- Goetzendorff, E., CAKE - Hybrides Gruppenschlüsselmanagementprotokoll für RIOT OS, Ludwig-Maximilians-Universität München, 05, 2018.
- Yosofie, M., CAKE - Hybrides Gruppenschlüsselmanagementprotokoll für RIOT OS, Ludwig-Maximilians-Universität München, 05, 2018.
- Engelbrecht, W., Group Key Management with Strongswan, Ludwig-Maximilians-Universität München, 01, 2018.
- Rehms, S., Dezentrale Datenverteilung mit TPM-basierter Authentifizierung , Ludwig-Maximilians-Universität München, 01, 2018.
- Haslberger, K., Kim, D. H., Seil, S., Implementierung und Evaluation von WalnutDSA als Modul für FreeRTOS, Riot und Linux Kernel, Ludwig-Maximilians-Universität München, 12, 2017.
- Edmonds, K. O., IoT meets HPC: Securely transferring wireless sensor data to a supercomputer utilizing the LRZ Cloud, Ludwig-Maximilians-Universität München, 10, 2017.
- Pauls, P., Parallelization of AES on Raspberry Pi GPU in Assembly, Ludwig-Maximilians-Universität München, 07, 2017.
- Heider, T., Minimal G-IKEv2 implementation for RIOT OS, Ludwig-Maximilians-Universität München, 04, 2017.
- Eich, F., Bidirectional CAN bus telemetry on a Formula Student / SAE car, Ludwig-Maximilians-Universität München, 04, 2016.
- Guggemos, T., Performanceanalyse von IPSec und (D)TLS auf mobilen Geräten, Ludwig-Maximilians-Universität München, 07, 2013.
Contact
For further information or access to the testbed, please contact embedded-sec-lab@nm.ifi.lmu.de
 Dr. N. gentschen Felde |
 T. Guggemos, MSc |
 J. Schmidt, MSc |
 M. Höb, MSc |
 S. Grundner-Culemann, MSc |

![[PRINT]](/_images/printer1.png)
![[FLAG]](/_images/flag-en.png)