- ... people2.1
- or the processes on their behalf
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... objects2.2
- persons and users are both treated as objects
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... (obligation2.3
- In contrast to obligation policies by the Imperial
College, negative obligation policies are not used.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... discussions2.4
- Thanks to Cheh Goh, Adrian Baldwin and Marco
Cassasa Mont from the Hewlett-Packard Laboratories, Bristol
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... space2.5
- Authorisation policies express this by having
the domain scope expression ``any'' as subject.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...DAC3.1
- MAC stands for Mandatory
Access Control, DAC stands for Discretionary Access Control, and
I&A stands for Identification and
Authentication
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
OMT4.1
- Object Modelling Technique
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... delegation4.2
- Delegation and transfer of responsibility are used as follows:
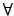 A delegate (resp R, B) A delegate (resp R, B) |
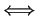 |
isresp (resp R, A) |
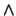 |
isresp (resp R, B) |
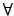 A transfer (resp R, B) A transfer (resp R, B) |
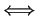 |
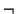 isresp (resp R, A)
isresp (resp R, A) |
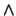 |
isresp (resp R, B)
|
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... Team6.1
- URL:
http://wwwmnmteam.informatik.uni-muenchen.de
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
functionality6.2
- The only exception to this is the Persistence
Service.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... DHCP6.3
- Dynamic Host Configuration Protocol
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... MAC6.4
- Medium Access Control - layer 2
in the ISO-OSI network reference model
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... additionally6.5
- The constraint expressions of the policy are
evaluated before the policy finally is enforced.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... policies6.6
- In subsection
![[*]](http://www.nm.informatik.uni-muenchen.de/common/icons/latex2html-97.1/cross_ref_motif.gif) an
ambiguity of the semantics between authorisation policies and
obligation policies as used in the NoCScontrol is discussed.
an
ambiguity of the semantics between authorisation policies and
obligation policies as used in the NoCScontrol is discussed.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... semantics6.7
- i.e. best effort, exactly once,
at most once, etc.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.